Online gambling firms are being targeted with ransomware by Chinese state-sponsored hackers in what is either a dramatic shift in priorities or simply greedy techs looking to pad their meager salaries.
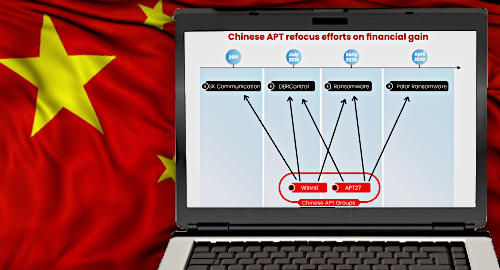
A report by Israeli cybersecurity firms Profero and Security Joes details a series of ransomware attacks against five unidentified online gambling companies earlier this year by a group alternately known as Advanced Persistent Threat 27 (APT27) or Emissary Panda.
The report builds on a separate report this February by Trend Micro, who identified a Chinese-led hacking group known as Winnti (aka APT41), which until that point had a history of going after online gaming (not gambling) firms. The APT27 attacks used similar DRBControl malware to gain access targeted servers but APT27 was traditionally focused on corporate espionage rather than financial gain.
The APT27 attacks also differed in that, once the hackers had gained access to a specific server, they utilized the BitLocker encryption tool built into Windows to deny access to the servers by their rightful owners rather than employ a custom piece of ransomware.
Profero/Security Joes’ reps say the hackers demanded a total of US$100m in Bitcoin from the targeted gambling operators to unlock the servers. However, no ransom was ever paid, as the security teams were able to minimize the threat and the companies were able to restore their data using backup files.
In 2019, US cybersecurity group FireEye claimed Winnti, the group cited in the TrendMicro report, had pioneered combining political and commercial activities dating back to 2014. FireEye couldn’t determine whether this group “enjoys protections that enables it to conduct its own for-profit activities, or authorities are willing to overlook them.”
China’s neighbor North Korea is notorious for engaging in these types of for-profit cyber-shenanigans, having not only established a network of its own online gambling sites, but also attempted to steal Bitcoin from South Korean cryptocurrency exchanges and is widely believed to have been behind the attempt to steal $1b from the Bangladesh government (they got away with ‘only’ around $81m).
However, pandemic aside, China’s economic situation isn’t anywhere near as dire as North Korea’s and cybersecurity researcher Amit Serper told Haaretz that China’s state-sponsored hackers tend to use the same tactics and tools across a number of attacks, making their digital footprints relatively easy to track. That opens the possibility that another bad actor is attempting to disguise its true identity by mimicking Chinese tactics. So could North Korea be pulling a false flag operation here?
There’s also the possibility that the ransomware was simply a diversion and that the hackers’ primary aim was to disrupt operators accepting bets from mainland gamblers. China dramatically boosted its fight against ‘cross-border’ gambling last year and may have been looking for new ways of identifying and punishing mainland gamblers as a warning to others.
The hackers’ motivations may be unclear but the moral of this story isn’t. Cyberspace is a dangerous place, so let’s be careful out there, people.