Online video game portals are increasingly finding themselves under malicious cyber-attack as COVID-19 forces individuals – not all of them honourable – to seek out digital forms of entertainment.
The third-quarter threat report from distributed-denial of service (DDoS) mitigation specialists NexusGuard found that real-money online gambling and free-play/virtual currency online gaming operators were the two most popular DDoS targets in Q3, although the real-money boys are doing a much better job at defending their turf than their recreational counterparts.
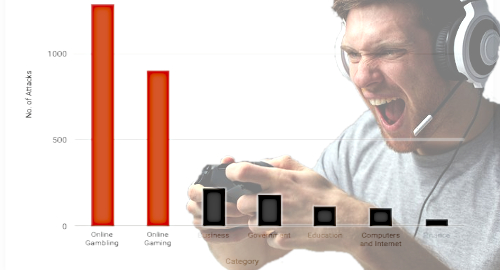
NexusGuard’s numbers show online gambling accounted for 45.2% of all DDoS attacks in the three months ending September 30, while online gaming accounted for 31.7%. Non-gaming sectors such as business, government, education and finance were subject to dramatically fewer attacks.
The report claims the overall number of attacks remains high, up over 287% from Q3 2019, but represented a 51.3% fall from Q2, during which the pandemic lockdown was more severe and individuals came to rely more heavily on digital connectivity, particularly in terms of entertainment options.
While the report credits online gambling ops for being “very well versed” in ensuring their systems are robust enough to repel DDoS attacks, the same can’t be said for online gaming outfits. And with online gaming platforms “extremely sensitive to latency and availability issues,” they’re effectively DDoS catnip.
Worse, apart from organized hackers attempting to extort platforms, the report fingers online gamers themselves for utilizing surprisingly cost-effective DDOS-for-hire services to target rival players. The report cites French company Ubisoft seeing a sharp increase in January targeting its Rainbow Six Siege game, due to a recent reset of global player rankings that convinced some players to target rivals for attack, forcing them to disconnect and handing the attacker the win.
The online gambling industry remains subject to “significantly more complex” attacks, with 41.5% of attacks being multi-vector assaults, while only 6.4% of online gaming attacks were multi-vector. Nearly 73% of Q3’s DDoS attacks didn’t exceed 90 minutes in duration, while 1.25% exceeded 1200 minutes, with one particularly persistent attack lasting 34,551 minutes.
China was the largest source of attacks in Q3 with nearly 32% of the total, with runner-up Turkey (13.9%) narrowly topping the US (13.75%). The remainder of the top-10 were entirely comprised of Asia-Pacific regions.