 US-facing online sportsbook BetOnline was knocked offline last weekend by a distributed denial of service (DDoS) attack, as the scale of these attacks grows to previously unimaginable heights.
US-facing online sportsbook BetOnline was knocked offline last weekend by a distributed denial of service (DDoS) attack, as the scale of these attacks grows to previously unimaginable heights.
On Friday, BetOnline account holders began reporting that they could no longer access the site. While BetOnline’s official Twitter feed insisted the company’s IT team was working to remedy the “network issues,” the site remained offline for a couple days, leaving the site’s customers venting all manner of expletives in gambling forums.
On Monday, BetOnline management shared a statement with the SBR forum, indicating that the outage was the result of “an attempt by a third party to disrupt traffic and site access,” confirming many account holders’ suspicions that the site was undergoing a sustained DDoS attack.
Online gambling sites, particularly sports betting sites that depend on time-specific events, have long topped the list of targets favored by DDoS attackers. Poker sites’ well-publicized tournament schedules are also tempting targets, and while we take PartyPoker at its word that its unplanned downtime last Sunday was due to a ‘server malfunction,’ one may never know for sure whether or not the issue was the result of external actors.
Sites targeted by DDoS attacks are usually reticent about acknowledging this reality because like attracts like. Other DDoS dickwads make note that a site’s DDoS defenses aren’t up to scratch, making them more likely to suffer downtime and also more likely to pay the demanded ransom for allowing the site to resume activities with its customers.
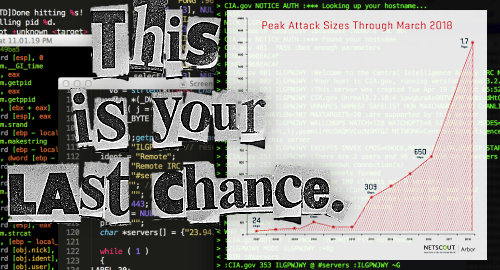
Last year saw the rise of DDoS botnets of unprecedented size, thanks to hundreds of thousands of unsecured Internet of Things (IoT) devices. But last week saw the rise of a new, even larger DDoS attack system that likely spells future trouble for a great many online gambling operators.
On March 1, online security firm Akamai reported an unprecedented 1.35 terabits per second (Tbps) attack against web-based hosting service Github, which was briefly forced offline before Akamai was able to ‘scrub’ the incoming traffic clean of malicious data. (Read Github’s post-mortem of the event here.)
The new DDoS method uses a new reflection and amplification vector called memcaching, which caches data to lighten the burden imposed by memory intensive services. Memcaching has the capacity to amplify attack volume by a factor of 50k through the control of open memcached servers accessible on the public internet.
On Monday, DDoS mitigation service Arbor Networks reported an even larger 1.7Tbps attack against an unspecified client of a US service provider that also used the memcached amplification method. Amazingly, the service provider was able to blunt the attack with no outages reported by the client.
Bottom line, customers of any gambling site that lacks these internet giants’ robust DDoS defenses can likely expect more unexpected downtime in the near future. Brave new world, people.