 Fraudsters are increasingly posing as online bookmakers to encourage victims to click on links that will infect their computers with malware or lead them to sites where their banking info will be stolen.
Fraudsters are increasingly posing as online bookmakers to encourage victims to click on links that will infect their computers with malware or lead them to sites where their banking info will be stolen.
A new report by cybersecurity solutions provider Group-IB details the types of threats it has seen in malicious emails during the first half of 2020. The company says it blocked 9,304 phishing web resources in H1 2020, up 9% over the first half of 2019.
Disturbingly, Group-IB says 69% of these resources used safe SSL/TLS connection, up from 33% at the end of 2019. Sites lacking SSL/TLS certificates are often flagged by web browsers before a victim is allowed to proceed, thereby diminishing the effectiveness of phishing efforts, but fake or forged certificates are increasingly available on the dark web.
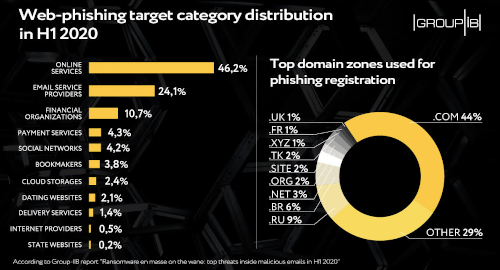
Emails purporting to come from legit online services accounted for 46.2% of malicious emails, while email service providers ranked second with 24.1%. Financial organizations (10.7%), payment services (4.3%) and social networks (4.2%) filled out the top-five.
Emails purporting to come from online bookmakers ranked sixth with 3.8%, nearly twice the amount claiming to be from dating sites. Individuals directed to these bogus bookies might bang in their account information without thinking twice, after which their real betting account – not to mention their credit cards and other banking channels – could be pillaged at will.
(Australia’s telecom watchdog recently issued a warning about malware in emails from internationally licensed online casinos, but that warning came as part of a wider campaign to paint any non-Australian site as crawling with cooties, so take it with a grain of salt.)
Getting back to the report, Group-IB says nearly half (44%) of the web domains used in these phishing attempts were of the dot-com variety, while the highest country-specific domain was Russia at 9%, ahead of runner-up Brazil at 6%.
The pandemic hasn’t been kind to the online gambling industry in terms of security, with the monthly number of distributed denial of service (DDoS) attacks undergoing a five-fold increase between February and May of this year as the lockdowns took hold and online activity rose.
If there’s an upside to this story, it’s that Group-IB said only 1% of emails it analyzed contained ransomware, a sharp decline from the second half of 2019, during which ransomware was in every second email. This is apparently due to ransomware operators shifting from mass attacks to targeted efforts at corporate networks.
Ransomware’s former role as top malware dog was taken by spyware, which was found in 43% of analyzed emails. Downloaders (which install additional malware) ranked second with 17%, followed closely by backdoors offering remote access to victims’ computers (16%) and banking Trojans (15%).
Online gambling operators are also advised to ensure staff take appropriate care before clicking on links or opening email attachments. Some Asian-facing sites learned that lesson the hard way last year. US-facing sportsbook BetUS had purloined data published online this spring, and clients of sportsbook provider SBTech were forced offline around the same time after an unspecified attack hit the company.
Land-based casinos are also increasingly under fire from malicious agents. Iranian hackers targeted Las Vegas Sands’ Pennsylvania casino several years ago, while multiple casinos in Canada were targeted by more fiscally-minded hackers. Just this month, the Sugar Creek casino in Oklahoma was forced to shut after an unspecified ‘network security incident’ over the Labor Day weekend. To paraphrase a certain red woman, the net is dark and full of terrors.





